CyberSecStats #36 - What's putting CISOs under pressure, android malware trends, and phishing in Japan.
CyberSecStats, is a weekly round of the latest cybersecurity statistics and industry trend data. This week’s issue is brought to you by Paubox
Hello!
Laura from CyberSecStats here.
This week, we added 20 newly published reports to our database, covering a range of topics from CISO burnout rates to the rise of AI-generated code in production systems.
As always, thank you for subscribing.
Outsmart email attacks
Paubox blocks phishing and helps keep email HIPAA compliant. Setup is quick.
Send and receive secure email with Google Workspace or Microsoft 365. Meet HIPAA requirements and protect patient data. No IT team or portals required.
This Week's Cybersecurity Eye-Openers
1. AI code is everywhere, but so is AI uncertainty
100% of organizations now have AI-generated code in their codebases, yet 81% lack full visibility into how and where AI is being used across the software development lifecycle.
2. CISOs feel under siege
73% of U.S. CISOs faced a significant cyber incident in the past six months, with two-thirds reporting that they feel burned out on a weekly or daily basis. Management is partly responsible - 44% of CISOs rank board or executive expectations as their number-one stressor.
3. Cloud identities are dangerously over-privileged
99% of cloud identities were found to be over-privileged, with 44% of true-positive security alerts driven by identity-related weaknesses.
Big Picture Reports
2026 CISO Perspectives Report (Portnox)
CISOs feel largely unprepared for the new security challenges created by rapidly growing AI use.
The shift:
- The percentage of companies constantly re-evaluating tools to improve cyber insurance premiums dropped from 68% in 2024 to 40% in 2025.
- 78% of CISOs lack a formal strategy for handling AI identities in a zero-trust security architecture in 2025.
- 78% of CISOs expect AI to create a moderate or significant amount of new IT or security work for their teams due to AI-related security risks and vulnerabilities.
Read the full report here.
2025 CISO Pressure Index (Nagomi Security)
More data on the real impact of AI-related incidents and the pressure they put on security leaders
The breaking point:
- Nearly 20% of recent incidents reported by CISOs were already AI-related.
- 39% of CISOs say they often feel blamed, even when incidents fall outside their direct control.
- 44% of CISOs rank board or executive expectations as their number one stressor.
Read the full report here.
Cybersecurity Forecast 2026 (Google Cloud Security)
Data leak site activity hit record highs thanks to nation-state actors, but Russian state-backed cybercrime is on the decline.
The threat landscape:
- The number of victims listed on data leak sites reached 2,302 in Q1 2025, the highest single-quarter count observed since tracking began in 2020.
- North Korean cyber threat actors executed the largest recorded cryptocurrency heist valued at approximately $1.5 billion.
- A decline in disruptive and destructive Russian cyberattacks has been observed since 2022.
Read the full report here.
AI & Code Security
Digital Fraud and Abuse Report 2025 (Akamai)
An explosion in AI bot traffic means that organisations are struggling to distinguish between legitimate users and automated threats.
The bot surge:
- AI bot traffic surged by 300% from 2024 to 2025.
- The publishing industry experienced 63% of AI bot triggers within the broader digital media industry.
- The commerce industry recorded more than 25 billion bot requests over a two-month observation period.
Read the full report here.
Featured report
State of Dependency Management 2025: Security in the AI-Code Era (Endor Labs)
AI coding assistants bring dodgy dependencies into your development pipeline.
The dependency crisis:
- Only 20% of dependency versions recommended by AI coding assistants were found to be safe to use in 2025.
- 44-49% of dependencies imported by AI coding agents contained known security vulnerabilities.
- About 75% of the more than 10,000 Model Context Protocol (MCP) servers were built by individuals without enterprise-grade protections.
Read the full report here.
State of Product Security for the AI Era 2026 (Cycode)
Shadow AI-generated code exists in every organization.
The visibility gap:
- 100% of organizations have AI-generated code in their codebases.
- 81% of organizations lack full visibility into how and where AI is being used across the software development lifecycle.
- 30% of organizations say AI now creates the majority of code in their organizations.
Read the full report here.
Email Security
2025 healthcare email security report
Insights from 180 email-related healthcare breaches and actionable steps to protect your organization.
- Why only 1.1% of organizations have a 'Low Risk' email security posture
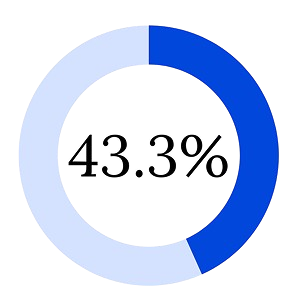
- 43.3% of email attacks involved Microsoft 365
- 264% increase in ransomware attacks targeting healthcare
Actionable data about the email security risks facing healthcare providers in 2026
State of Misdirected Email Prevention (Abnormal AI)
Human error in emails (i.e., sending them to the wrong address) is driving data loss.
The email mistake crisis:
- 96% of organizations experienced data loss or exposure from misdirected emails in the past year.
- Misdirected emails accounted for 27% of all data protection incidents under the GDPR last year.
- The average enterprise spends over 400 hours per year managing false positive alerts from data loss prevention tools.
Read the full report here.
Data Security
2025 Data Security Landscape (Proofpoint)
A mixture of Gen AI adoption and existing insider risks is creating a data security hurricane.
The “perfect storm”:
- Just 1% of users are responsible for 76% of data loss events.
- 58% of organizations attribute their most significant data loss events to careless employees or third-party contractors.
- Over a quarter (29%) of organizations saw their data grow 30% or more over the past year.
Read the full report here.
Cloud
Building Cloud Trust: How trust and security are shaping the next phase of cloud growth (VansonBourne)
More organizations feel that public cloud is more secure than on-premises alternatives.
The cloud trust shift:
- Around 8 in 10 organizations report at least one data breach in the past year, both in on-premises infrastructure (78%) or in the public cloud (79%).
- 56% said the public cloud was best positioned to deliver security, as opposed to 37% who chose on-premises, and 7% who responded that neither model was best.
- 51% said the public cloud was best positioned to meet regulations, compared to 41% who responded that on-premises solutions were best suited.
Read the full report here.
Too Much Trust: The Danger of Over-Privileged Cloud Identities (ReliaQuest)
Cloud identity misconfigurations create systemic risk as privilege escalation drives confirmed alerts.
The privilege problem:
- 99% of cloud identities were found to be over-privileged, creating significant security risks.
- 44% of true-positive security alerts from cloud security tools in Q3 2025 were driven by identity-related weaknesses.
- 52% of all confirmed identity-based alerts were due to identity-related privilege escalation.
Read the full report here.
Infrastructure Security
An X-ray of Modern Networks: Understanding and Mitigating IoT Security Risks (Forescout)
Non-traditional IT devices are increasingly dominating enterprise networks as vulnerability management becomes increasingly complex.
The IoT sprawl:
- 65% of devices across organizations are classified as non-traditional IT.
- 11% of devices across organizations are classified as network equipment.
- There are 3,200 unique operating system versions observed across organizations, averaging 876 versions per organization.
Read the full report here.
Zscaler ThreatLabz 2025 Mobile, IoT, & OT Threat Report (Zscaler)
Android-powered devices are in the crosshairs for malware developers.
The mobile and IoT threat:
- There was a 67% year-over-year increase in Android malware transactions.
- 239 malicious applications were identified on the Google Play Store, collectively downloaded over 42 million times.
- Adware accounted for 69% of mobile threat cases, overtaking the Joker malware family, which dropped to 23% of cases.
Read the full report here.
Passwords
Minimum password requirements met: Top 1,000 most-visited websites (NordPass)
Many of the world's most popular websites fail to enforce basic password security standards.
The password problem:
- 58% of the world's top 1,000 most visited websites do not require special characters for their passwords.
- 42% of the world's top 1,000 most visited websites do not enforce any minimum password length requirements.
- Only 1%, or five websites, among the top 1,000 most visited websites met all best-practice password criteria.
Read the full report here.
Enterprise Security
Enterprises Under Attack: Quarterly Threat Actor Patterns | Released Q3 2025 (Arkose Labs)
Automation is driving a rise in malicious traffic, which is getting more targeted, too.
The escalation:
- Malicious traffic surged nearly 20% from Q1 to Q2 2025.
- Average attack size grew by over 12% from Q1 to Q2 2025.
- Three-quarters (75%) of scams now target critical workflows such as account creation and sign-in processes.
Read the full report here.
Industry Deep Dives
US Healthcare Cyber Resilience Survey (EY)
Healthcare organisations are experiencing more operational, financial, and clinical disruptions than ever due to cybersecurity-related incidents.
The healthcare cyber crisis:
- Healthcare organizations experienced an average of five different types of cyber threats that impacted their organizations in the past year.
- 72% of healthcare organizations experienced a moderate to severe financial impact from cyber incidents in the past two years.
- 59% of healthcare organizations faced clinical consequences from cyber incidents, including delayed treatments and compromised patient trust.
Read the full report here.
The Higher Ed Innovation Index 2025 (Transact + CBORD)
Campus leaders struggle with outdated security technology as fraudulent enrollments rise.
The campus security challenge:
- 71% of campus leaders say outdated security technology puts student safety at risk.
- 28% of campus leaders say physical and digital security still operate in silos on their campus.
- 50% of higher education institutions are monitoring transactions in real-time to combat fraud.
Read the full report here.
State of Ransomware in Retail (Sophos)
Retailers pay ransoms at near-record rates. Median demands have doubled. But the good news is that recovery costs are falling.
The retail reality:
- 58% of retail organizations with encrypted data paid the ransom in 2025, marking the second-highest payment rate in five years.
- The median ransom demand for retail ransomware attacks doubled to $2 million in 2025 compared to 2024.
- 62% of retailers who experienced attacks restored their data using backups in 2025, the lowest rate in four years.
Read the full report here.
Regional Spotlight
ENISA Sectorial Threat Landscape - Public Administration (ENISA)
DDoS attacks are the biggest driver of EU public sector cyber incidents.
The public sector under attack:
- 38% of all reported cyber incidents in the EU in 2024 targeted the public administration sector.
- 60% of all reported cyber incidents in 2024 were Distributed Denial-of-Service (DDoS) attacks.
- Hacktivists were responsible for nearly 63% of cyber incidents in the EU in 2024.
Read the full report here.
2026 RSA ID IQ Report (RSA)
Though Japanese organizations are less likely than global peers to have experienced an identity-related breach and lead the world in passwordless authentication adoption, phishing remains their top and most concerning security threat.
The identity crisis:
- 71% of Japanese respondents identified phishing as the top threat facing their organization, significantly higher than the global average.
- Only 56% of Japanese respondents reported experiencing an identity-related breach in the past three years.
- Japan ranks #1 in the proportion of organizations using passwordless as the primary authentication method.
Read the full report here.
CrowdStrike 2025 European Threat Landscape Report (CrowdStrike)
Ransomware deployment accelerates across Europe.
The European surge:
- Ransomware deployment speed increased by 48% as observed in 2025.
- European organizations accounted for nearly 22% of global ransomware and extortion victims in 2025.
- Since January 1, 2024, more than 2,100 victims across Europe were named on extortion leak sites.
Read the full report here.